Sniffers: An Introduction
A sniffer, which can also be referred to as a network analyzer, is a piece of software that analyzes network traffic, decodes it, and gives it back packet information so that a network administrator can use it to help diagnose problems on the network. But because these tools can be so powerful, they can also help give leverage to those of the black hat world by allowing them to pull plain text information off the network as well (usernames, passwords, unencrypted emails, instant message chat, etc.).
Some of the more “legitimate” uses for a sniffer fall towards the roles of the network administrators. They can be used to probe the network for bandwidth usage, helping pinpoint which individual machines may be running malware or simply have wrong network settings. Sniffers are often used as a practical defense against finding intrusion attempts by detecting inappropriate traffic. If you’re ever going to be in a role where you need to ensure your network is protected, you would do well to learn how to use a sniffer. I recommend Wireshark (formerly known as Ethereal), it’s free (as in beer) and well supported with great documentation. Other alternatives are NAI Sniffer (commercial), TCPDump (*nix), WinDump (Win32), Cain & Abel, Dsniff, and Ettercap (the last three are more specialized for password extraction but can still be used to test your applications or network protocols).
Sniffers can also be used to bypass security. Many application protocols pass credentials in plain text or use weak encryption that is easy for a sniffer to decode. Common examples of insecure protocols are FTP, Telnet, POP3, SMTP, and HTTP Basic Authentication. Instead, secured/encrypted protocols should be used, SFTP, SSH, HTTPS (SSL).
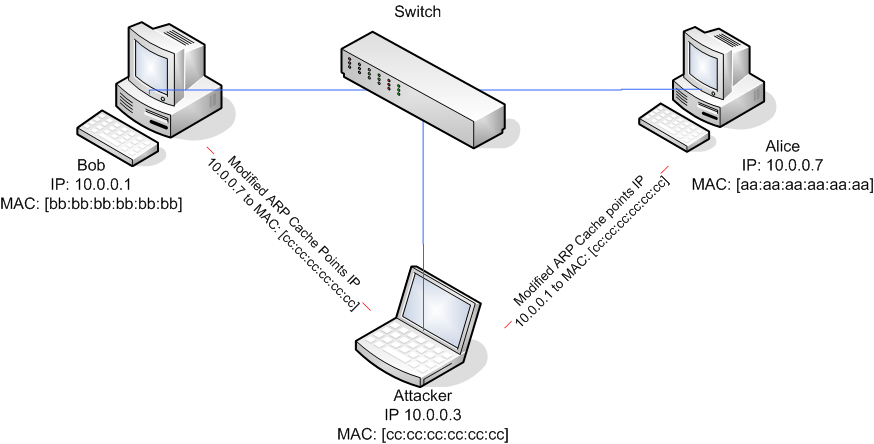
One of the most common hacks other than password sniffing that sniffers can be used for is probably ARP Spoofing / ARP Poisoning. ARP (Address Resolution Protocol) allows the network to translate IP addresses into MAC addresses. Essentially, when one host using IP on the LAN is trying to contact another, it needs the MAC address of the host it is trying to contact. It first looks in its ARP cache to see if it already knows the MAC address. Otherwise, it sends out an ARP request (looking for the IP).
To view your ARP cache:
Windows Command line: "arp -a"
Linux Command line: "ip neigh show"
In common bus networks like a wired hub or 802.11b, all traffic can be seen by all hosts whose NICs are in promiscuous mode, but not on a switched network. A switch looks at the data sent to it and only forwards packets to the intended recipient based on the MAC. This helps secure the network by only sending packets to where they need to go. Of course, I wouldn’t mention this if there wasn’t some sort of way around it. Programs like Arpspoof (part of the Dsniff package), Ettercap, or Cain & Abel can allow you to fool the network and allow you to spoof another machine making the network think you have the IP it is looking for, then funnel their traffic through you.
So, even with a switched network, it’s not too difficult for an attacker to simply boot up their BackTrack CD, do some ARP spoofing with Dsniff or Ettercap, and redirect traffic through them for the purpose of sniffing.
So how can one help ensure their network doesn’t fall to these attacks?
- Avoid using insecure protocols like Basic HTTP Authentication and Telnet. You should make it a practice to sniff your own network to see what information is being passed and ensure you’re not already sending sensitive information across the network.
- If you do have to use an insecure protocol, tunnel it through a secure channel (SSH, SSL, etc.)
- Look into using Static ARP tables between critical workstations and servers. Although a pain to maintain, they do limit the chances of ARP spoofing.
- You can run software like ARPWatch to detect changes in MAC addresses on the network.
- Try running tools that can detect if a NIC is running in promiscuous mode, this could be a sign of sniffing. (Sniffdet and Sentinel are common tools)
- All mobile or guest access points should use a VPN to connect to the network.
- Better yet, keep public terminals on a separate LAN from workstations and servers.
- Lockdown workstations so that users can’t install sniffing software or boot from live CDs (BackTrack, Knoppix, etc.)
Each Thursday, Security Musings features a security-related technology or tool. Featured items do not imply a recommendation by Gemini Security Solutions. For more information about how Gemini Security Solutions can help you solve your security issues, contact us!