Mozilla’s Firefox 3 New SSL Policy – Is This The Right Way?
Many people have been praising Mozilla’s Firefox 3 ever since pre-beta. I can easily throw myself onto that band wagon, but there is one feature that has been causing a little commotion, and I again can easily agree with the commotion.
Firefox 3 (FF3) limits usable, encrypted (SSL) web sites to those that have an approved digital certificate from an authorized vendor of Mozilla’s choosing, making it so you have to pay to be recognized. What’s the big deal?
When you visit an encrypted site in FF3, and that site uses a self-signed or simply unapproved certificate, FF3 doesn’t immediately show the page. Instead, you are greeted with what, at first glance, would seem to be an error page.
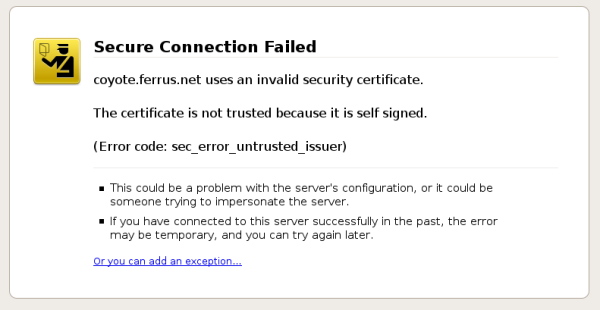
In order to move beyond this page and actually continue to the site as intended, you need to process through 4 clicks to add that site as an “exception.”
The use of a certificate is for SSL – which has two main purposes – allow connections to be encrypted so they can’t be snooped, and allow sites to be authenticated so they can’t be impersonated. Advocates of Mozilla’s policy seem to only focus on the latter, stating that a self-signed certificate has no value for authenticating a web site. The real concern is that snooping is much more of an easily attainable threat than impersonation. So, it is much more valuable to have a self-signed certificate than nothing at all, but doing so puts FF3 users at an inconvenience.
This, to me, sounds like it is blatantly going against the notions of Net Neutrality, something that has been fought to keep open for ages. Something like this completely discriminates against those not willing to purchase an “approved” certificate.
7 thoughts on “Mozilla’s Firefox 3 New SSL Policy – Is This The Right Way?”
So, create an exception. This isn’t against net neutrality. This is about protecting users from themselves, which they desperately need to have happen.
Even older versions of Firefox would present a warning or error message when an invalid certificate is presented, allowing you to click something to continue. IE also has a quickly dismissible warning. All this is doing is making the user have to make a serious security decision before continuing. It is no different than “Vista UAC”:http://securitymusings.com/article/177/why-you-dont-want-to-disable-uac which I have previously ranted on — it’s a *good* thing!
I’m on the fence about this one – most people don’t know what the heck this is.
It’s like posting a warning sign outside of a swamp in German. You know there is something in the lake, but ignore the sign since you can’t really make heads or tails of it. Is it a cougar, a crock, or just a no-littering sign?
I like the “phishing” bar (used in IE) which seems to be more effective and understandable to the average Joe or Jörn 😉
This crap goes well with their crooked logic.
For example, they show the “What’s New” page AFTER update has been installed. Talk about common sense — you read “What’s New” to find out whether you want to update or not. There is no point in reading it after the fact when you can’t roll back to the previous version.
As for this particular “security” measure — Mr. Peter should go buy a clue if he believes that this nagging is any good for the end user let alone for the advanced ones.
Peter, you say “This is about protecting users from themselves”, but this is just bad design. Just check the choice of words:
1. “Failed” — this is misleading, the connection has not failed, you refused to make it.
2. “Not trusted” — you don’t trust it but what about me?
3. “Could be a problem with the server’s configuration” — misleading again.
4. “may be temporary, and you can try again later” — as if that will actually fix the problem! Misleading yet again.
5. “Or you can add an exception…” — Translation: “If we haven’t convinced you to give up by outright lying about what is going on in the above 5 paragraphs of big, fat, and misleading text then damn you Average Joe — you can proceed but we will make it as hard for you as possible.”
So Peter, it is not just a matter of creating exceptions (and some of us would need to create a lot of them) — it is about turning what used to be a warning sign into an obstacle.
As it was already pointed out, it is much harder to impersonate than to spy.
Remember, if someone goes through so much trouble to impersonate someone else, they will do it using a trusted certificate so this message won’t even get shown and thus it won’t be able to protect the user from an impostor.
Therefore, one can conclude that it is only preventing people from using SSL so their communication can be freely snooped by the third parties.
@Peter
“This isn’t against net neutrality. This is about protecting users from themselves”
“[This isn’t about claiming to know better than users. This is about claiming to know better than users.]”
Net neutrality is socialism. Net Neutrality is nanny-state.
What you have proposed, Peter Hesse, is the essence of socialism. Bravo?
@IGOR
Would you have it display What WAS new? or What is NOW new for you? 😉
I agree: it would be better to show a ‘why you might want to upgrade now’ drop down (same place as unapproved extension location)
..
A cert warning should show not merely for mismatch but ALSO for md5 signatures.
NoScript ABE has many features than should be native to the browser, much as with those in RequestPolicy
Comments are closed.