HP SWFScan Tool – Adobe Flash Application Security Scanner
One of the most expanded targets lately in vulnerability research is Adobe’s Flash. It has become a common everyday occurrence on the web; everything from banners, to games, to file uploads. It’s almost hard to find a mainstream site that doesn’t have some sort of flash application running somewhere within the domain. As a result it has become a target for many attacks. But one thing that hasn’t increased is the amount of time and checking that goes into the flash applications to ensure they are secure.
HP has been kind enough to release SWFScan, a .swf scanning utility that can de-compile applications built in Flash to extract the ActionScript code and statically analyze it to identify security issues. Some of the key items it can report on are:
- Information disclosure (CC numbers, Personal information, etc)
- Improper security calls (Security.allowInsecureDomain(), LocalConnection.allowDomain(), Security.allowDomain(), etc)
- Database connection string leakage.
- Inclusion of private keys for encryption
- Insecure flash storage object.
- XSS through FlashVars
- MD5 Hash detection.
- Source code path disclosures.
- And plenty more…
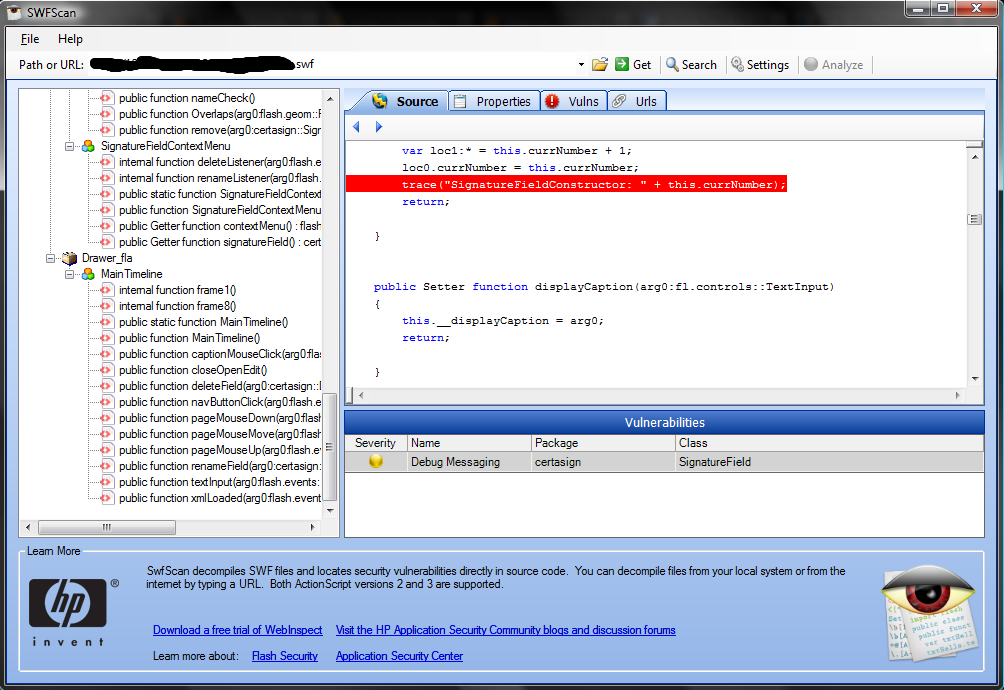
What it really breaks down to is swf files are not protected. It is quite easy to decompile them so you have to be very careful as to what information you include, collect, or expose within the code. But if you’re curious as to the current state of your flash applications, or even those that you might happen to use on a daily basis, HP’s SWFScan can be used to help assist in the discovery phase.
Each Thursday, Security Musings features a security-related technology or tool. Featured items do not imply a recommendation by Gemini Security Solutions. For more information about how Gemini Security Solutions can help you solve your security issues, contact us!