Changing Your Windows OS Fingerprint
With Windows holding 89.6% of the global market share, it is a very large target. This is one of the reasons Windows is targeted so much by malicious attacks. Not very hard when you’re such a big target. So, what if you could change that and make your Windows machine/server appear as something else, even to the most notable of sniffing tools (Nmap, P0f, Ettercap, etc.)? Well, you can.
In Windows XP and Vista, along with the server lines 2003 and 2008, you can make registry changes to the IP stack to change what identity you are putting out.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\DefaultTTL
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Tcp1323Opts
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\EnablePMTUDiscovery
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\TcpUseRFC1122UrgentPointer
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\TcpWindowSize
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\SackOpts
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\*\MTU
To help make these changes though, Adrian Crenshaw, aka “Irongeek,” has put together a handy tool for us – OSfuscate. It allows you to select exactly what OS fingerprint you’d like to replicate which includes a long list: BeOS, Checkpoint Firewall, DOS, FreeBSD, HP Unix, IBM OS400, IRIX, Linux, Novell, Palm OS 3.5, PalmOS 5.2, Playstation, Sega Dreamcast, Sun OS, Tru64, Windows 2000, Windows 98, Windows CE, Windows NT and Windows SP SP1. Yes, you saw correctly. You can make your Windows XP machine look as though it’s a Sega Dreamcast.
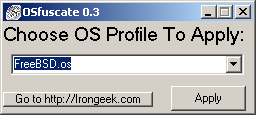
The author also points out that there is an additional parameter that can be found from sniffing the DHCP queries that can still identify you as a Windows machine; he also provides a tool that will patch the dhcpcsvc.dll to remove the identifying parameter (“MSFT 5.0”).
I put it to a simple test with nmap as my sniffer and using a Windows Server 2003 VM as a test bed.
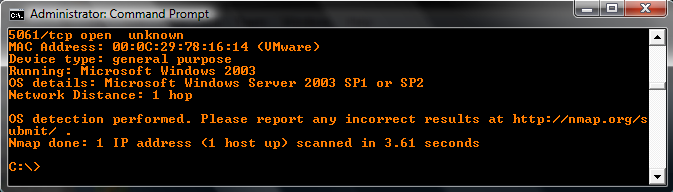
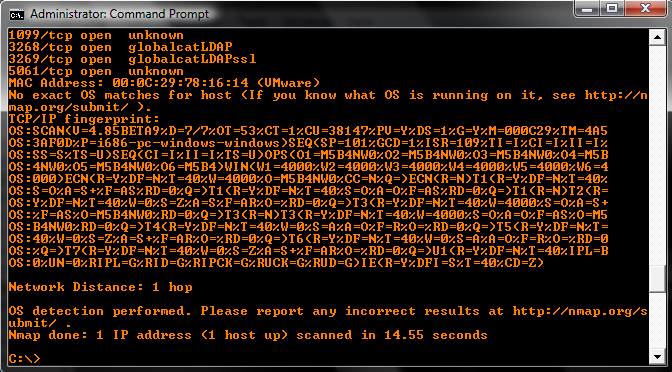
A strong reminder though that this is only security through obscurity. This by no means is a foolproof change, and your system is still vulnerable to any malicious attacks if they are targeted directly at you (and your system is un-patched). It simply makes the attacker’s job a little harder by not narrowing down the list of targets for them, and most of the good attackers know of tools / changes like these and will run an entire slew of attacks anyways. But it might help keep some of the script kiddies at bay.
2 thoughts on “Changing Your Windows OS Fingerprint”
Why isn’t this working for me?!
You’ll have to be a little more specific.
Comments are closed.