Sniffing Networks Part 3 – Understanding what you’re seeing
This continues part 1 and 2 of our Sniffing Networks series. This part is a little bit more technical, and a solid understanding of the concepts in Part 1 and Part 2 of this series is recommended.
Now that you have the concept of ARP spoofing down and how MAC addresses translate to IP addresses, you can actually start sniffing. There are many tools that will do all of this for you, but we’ll get to those in a later part. I feel that it’s essential that you understand what those tools are doing before you use them. Instead we’ll use Wireshark (Ethereal) to look at raw packets to understand what we’re actually seeing on the wire. First things first, if you don’t already have Wireshark installed, go get it. It’s available for Windows, OS X and most flavors of Unix (the GUI runs under X11, so you might need to set that up). Also, you’re going to see more interesting things if you have a *wired* Ethernet connection rather than a wireless one.
Start up Wireshark. Make sure you’re not running VMware/Parallels/etc. If you’re running under OS X look here for how you can see any interfaces). First, make sure you have some interfaces to sniff on. Go to Capture->Interfaces.
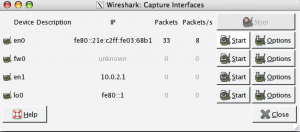
You’ll see a list of all interfaces on your system. In my case, en0 is my wired Ethernet (and the primary network connection for this machine). Go ahead and click on “Start” to start sniffing on this interface. Suddenly the main window will fill with all kinds of stuff, so what the heck is it? (Feel free to click Stop at any time)
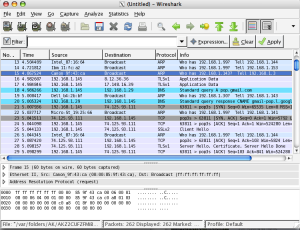
This screenshot is from our office network, so you’re not likely to find any clear text passwords in it (unless the protocol doesn’t support non-clear text passwords). You’ll see quite a few ARP requests at the beginning, as several machines are looking for the .30 computer (which is our domain controller). The main window shows all of the packets that were captured in a terse format. The bottom sections show the raw packet (in hex), and for each type of packet Wireshark knows about, it’ll break down the packet for you in easy to read chunks. The following screenshot is with the ARP packet detailed information expanded. Since we talked about it last time, it might make the most sense to you if you haven’t seen other types of packets.
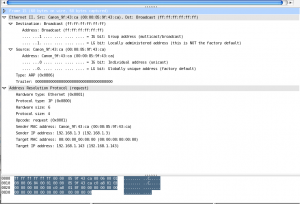
The ARP packet is from a printer to the broadcast Ethernet address (ff:ff:ff:ff:ff:ff) asking about 192.168.1.143. You can view the Ethernet packet “wrapper”, and then the actual ARP request which is using IP. Later on in the stream, you should see a response to this packet. Unless you’re debugging the network or verifying that any packets you sent out did in fact make it on the network, most people ignore ARP requests and the TCP/IP headers for packets. What you’re interested in is the content of those TCP packets. Wireshark shows these too!
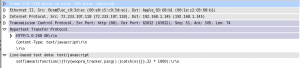
This screenshot shows some HTTP traffic. IP address 72.233.107.118 sent to 192.168.1.145 an HTTP response of 200 and then sent some JavaScript code. Now, once you’re at this level, you will need to be familiar with all of the protocols you want to understand. HTTP is an important one. You might want to also consider learning about AOL’s AIM protocol (they don’t encrypt passwords), POP, and IMAP. Those are the ones likely to net you some passwords in the clear.
The last feature of Wireshark that merits a discussion is “Follow the HTTP stream.” TCP/IP packets are limited in size, so you might not get all of the request or response in one packet. Wireshark will “glue” them together for you. Select the request or response you want to follow, and then right click and “Follow TCP stream”. A new window will pop up that shows you what the full “conversation” was.
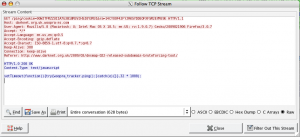
This is where you’re going to find passwords or other useful information (such as what a popular web application is on that network).
Stay tuned for part 4 where I’ll go over “easy” tools that just show you passwords, and you don’t have to think too much about what you’re sniffing.
Each Tuesday, Security Musings features a topic to help educate our readers about security. For more information about Gemini Security Solutions’ security education capabilities, contact us!
2 thoughts on “Sniffing Networks Part 3 – Understanding what you’re seeing”
Does my mac adresse change if I upgrade my computer with some other hardware? For example change the graphic card?
Comments are closed.